I'll give you the ones that you should know so far:
- EAX, ECX, and EDX are registers that you (the ASM hacker) can use for practically any purpose.
- ESP points to the top of the stack.
- EBP points somewhere else inside the stack. You use it to access values in the middle of the stack, including function arguments.
- ESI, EDI, and EBX are registers that we're not going to worry about now.
Not all registers follow the 3-letter format. Here are some new ones:
| Register Name | Size | Description |
|---|---|---|
| AX | 16 bits | Lower half of EAX. |
| CX | 16 bits | Lower half of ECX. |
| DX | 16 bits | Lower half of EDX. |
| AH | 8 bits | Upper half of AX. |
| CH | 8 bits | Upper half of CX. |
| DH | 8 bits | Upper half of DX. |
| AL | 8 bits | Lower half of AX. |
| CL | 8 bits | Lower half of CX. |
| DL | 8 bits | Lower half of DX. |
Those are the common ones you'll be using. Now you know that 16-bit and 8-bit registers exist in addition to the regular 32-bit registers.
Here are some new uncommon registers that you probably won't use. I'll give them to you anyway.
| Register Name | Size | Description |
|---|---|---|
| BX | 16 bits | Lower half of EBX. |
| BH | 8 bits | Upper half of BX. |
| BL | 8 bits | Lower half of BX. |
| SP | 16 bits | Lower half of ESP. |
| BP | 16 bits | Lower half of EBP. |
| SI | 16 bits | Lower half of ESI. |
| DI | 16 bits | Lower half of EDI. |
What about the "upper half" and "lower half" stuff? Well, the 16-bit and 8-bit registers are not independent of the big 32-bit registers.
Instead, you can think of the small registers as being pieces (or slices) of the big ones.
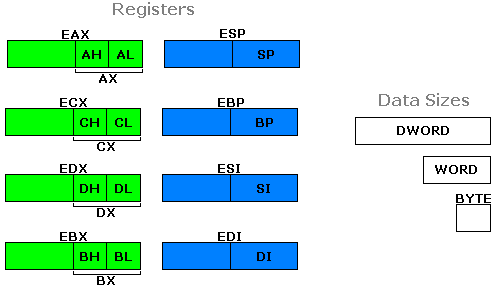
So let's begin some examples to make the idea of "register slices" more understandable.
The Small Registers
MOV EAX,11223344 ;Store hex number 11223344 to EAX. MOV AX,0 ;Store 0 to AX, which changes EAX to 11220000. MOV AL,5B ;Store 5B to AL, which changes AX to 005B and EAX to 1122005B. MOV AH,CC ;Store CC to AH, which changes AX to CC5B and EAX to 1122CC5B.
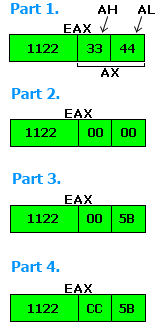
We see that AX is truly the "lower half" of EAX, meaning the lower 4 hex digits. AH and AL are the size of bytes, and they can only hold 2 hex digits. They each take up one-fourth the wideness of EAX, or one-half the wideness of AX.
Other registers work the same way. Here is an example using EDX:
MOV EDX,10000 ;Store 00010000 to EDX. MOV DH,95 ;Store 95 to DH, which changes EDX to 00019500. DX holds 9500. ADD DX,120 ;Adding 120 causes DX = 9620 and EDX = 00019620. SUB DL,F ;DL now holds 11, which means EDX = 00019611.The reason I'm telling you about these small registers is because they are sometimes used in the original Cave Story code.
An example of this:
Address Instruction 004799CD MOV WORD [4BBB54],AX ;Store contents of AX into WORD [4BBB54]. 004799D3 MOV ECX,DWORD [EBP-9C] 004799D9 MOV EDX,DWORD [EBP-9C] 004799DF MOV EAX,DWORD [EDX+40] 004799E2 MOV DWORD [ECX+20],EAXMost of the time however, you will still be working with the traditional registers EAX, ECX, and EDX.
Special Registers
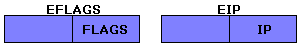
Here are some registers that I neglected to mention before. They are EIP, EFLAGS, IP, and FLAGS.
EIP is a 32-bit register (DWORD sized) that keeps track of which address the program is currently at.
EFLAGS is also 32-bit, and it keeps track of conditional ASM flags, which are modified by commands such as CMP and then used by commands such as JNE, JGE, and so on.
FLAGS is just the lower half of EFLAGS, and IP is the lower half of EIP.
OllyDbg will often abbreviate EFLAGS as EFL and FLAGS as FL.
Now, normally you never have to worry about these special registers, because they can't be used inside any regular commands, except for a few.
DEC EIP ;OllyDbg doesn't accept this. EIP can't be used as a normal register. MOV EFL,8 ;OllyDbg doesn't accept this. EFLAGS can't be used as a normal register.
Previous Lesson: NPC Hacking 3
Next Lesson: Redefining Memory
Table of Contents